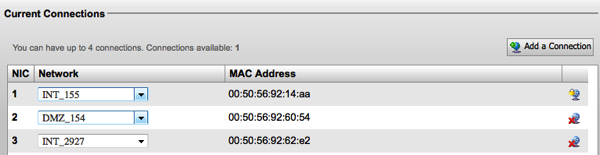
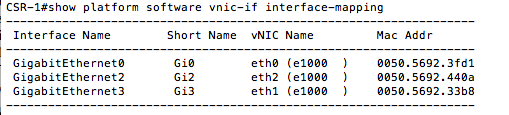
Cisco Services Cloud Router (CSR) 1000v is a virtual router you can deploy either in private/public cloud or in a virtualized data center.
One of the common use cases for the CSR 1000v is a secure VPN gateway in the cloud to terminate VPN tunnels. So if you run some applications in the cloud and you want to allow your branch offices to access those application over a secure network, you can run IPsec tunnels between those branch offices and the CSR 1000v in the cloud. From performance perspective this would work much better than back hauling the traffic to the data center (HQ) and then to the cloud.
In this post I will show you how to set up a VPN tunnel between Cisco CSR 1000v and a branch office router using Cisco Easy VPN. You may also use standard IPSec VPN but in my configurations I use Easy VPN because it’s, well, easier 🙂
The following configurations are part of a demo I gave at Cisco Live 2013 in Orlando where the CSR 1000v was the VPN server and the branch server (Cisco 2900 in this case) was the VPN client.
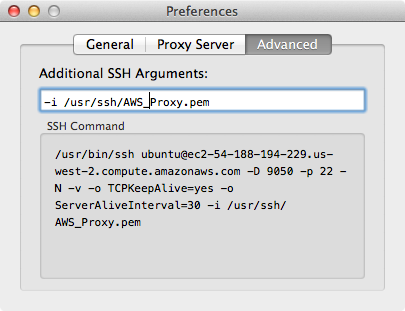
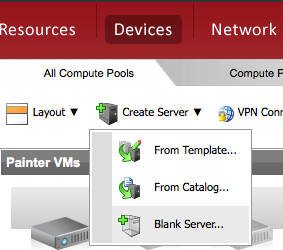
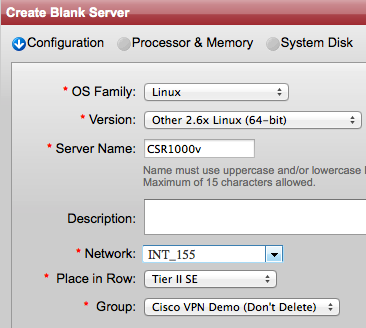
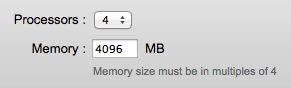
If you would like to learn how to install the CSR 1000v on Verizon Terremark eCloud, follow these steps in my post.
You will also need to open UDP port 500 and IP protocol ID 50 (ESP) on all firewalls sitting between the CSR 1000v and the branch router for the IPSec tunnel to be established successfully. Additionally depending on your design you may need to configure NAT.
In my setup, I’m using:
- Cisco CSR 1000v with IOS XE 3.9x running in Verizon Terremark Enterprise Cloud
- Cisco 2900 running IOS 153.2.T (branch office)
Here are the configs of the CSR 1000v (VPN Server). Only relevant configs are shown:
CSR-1#sh run
hostname CSR-1
!
aaa new-model
!
!
aaa authentication login hw-client-groupname local
aaa authorization network hw-client-groupname local
!
!
aaa session-id common
!
!
username myusername password 0 mypassword
!
!
crypto isakmp policy 1
encr 3des
authentication pre-share
group 2
crypto isakmp client configuration address-pool local dynpool
!
crypto isakmp client configuration group hw-client-groupname
key hw-client-password
dns 8.8.8.8
domain domain.com
pool dynpool
save-password
!
!
crypto ipsec transform-set transform-1 esp-3des esp-sha-hmac
mode tunnel
!
!
!
crypto dynamic-map dynmap 1
set transform-set transform-1
reverse-route
!
!
crypto map dynmap client authentication list hw-client-groupname
crypto map dynmap isakmp authorization list hw-client-groupname
crypto map dynmap client configuration address respond
crypto map dynmap 1 ipsec-isakmp dynamic dynmap
!
!
!
interface GigabitEthernet2
description WAN
ip address 10.22.36.71 255.255.255.224
negotiation auto
crypto map dynmap
!
interface GigabitEthernet3
description LAN
ip address 10.22.39.91 255.255.255.240
negotiation auto
!
ip local pool dynpool 192.168.1.1
!
!
ip access-list extended split_t
permit ip 10.22.39.0 0.0.0.255 any
!
end
Here are the configs for the Cisco 2900 router (VPN client).
no aaa new-model
!
ip cef
!
!
username vpntest password 0 vpntest
!
!
crypto ipsec client ezvpn hw-client
connect auto
group hw-client-groupname key hw-client-password
mode client
peer 10.22.36.71
username myusername password mypassword
xauth userid mode local
!
!
interface GigabitEthernet0/0
description WAN
ip address 10.35.120.104 255.255.255.0
duplex auto
speed auto
crypto ipsec client ezvpn hw-client
!
interface GigabitEthernet0/1
description LAN
ip address 172.16.4.102 255.255.255.0
duplex auto
speed auto
crypto ipsec client ezvpn hw-client inside
!
ip route 0.0.0.0 0.0.0.0 10.35.120.1
!
end
Note: You can also install the CSR 1000v as a VM in VMware Fusion or Oracle VirtualBox if you want to play.
Share This: